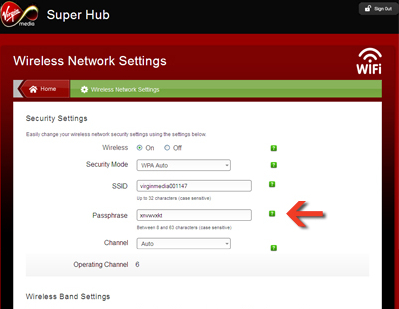
Double click the corresponding entry in the main panel. If there is more than one, look for the most recent one with a type matching 'AirPort network password'. Click the checkbox labelled Show password, and enter your user account password when prompted. The password will be displayed in the text box, where you can copy it as needed. In addition to authentication, wpa also provides for an encrypted channel over the wireless link. Mac filtering is just an acl; if you pass the filter you're in, but there's no encryption. I don't think these two are interchangeable as an either/or solution. Sent from Cisco Technical Support iPad App. WEP stands for Wired Equivalent Privacy. And this is the first wifi security, which was. Mac OS X WPA Password Cracker. Run Portable Penetrator via VMware fusion on Mac OS X. Mac OS X is a great choice when performing WiFi WPA Password Cracker pen testing auditing of clients WiFi Access Points. Apple deliver a high performance high end operating system that. When you subscribe to an Internet service, your Internet Service Provider (ISP) provides you with a network password. Look for this password on your wireless router or in the original paperwork that came from your ISP. The password might be labeled Wireless Key, security password, WPA2 password.
OK lets all take stock and use some logic here and I respectfully disagree with a few of the comments generally being banded about ! And i overall am unhappy about the general forum bashing as well as people may find a hint useful even though 'you' have not.
WPA-PSK / WPA2-PSK does not require an 'authentication server' per se as @leamanc has suggested.
Pre-Shared Key (PSK) Mode
The PSK mode is designed for home or small network use where an 802.1x authentication server isn't required. WPA-PSK works by regularly changing the automatic encryption keys authenticated between computers, your server or router and other devices that connect to it. PSK dramatically improves protection over WEP, as the encryption keys change very quickly, thus preventing intruders from gathering data to break encryption and into your network.
Now lets get to Encryption.....
WPA tends to use TKIP and WPA2 uses AES encryption.
Both these methods Apple call WPA Personal or WPA2 Personal.
AES is preferred as it is more secure and recent exploits of TKIP have led to it being slowly phased out just like WEP which should not be used at all.
However WPA works with most older hardware where as WPA2 will require more modern hardware (6 year old ish)
Overall with modern Wi-FI hardware using 'n' protocol you need to ONLY use WPA2 with AES encryption to get the best speeds/throughput. But that is another story.
I do not really want to go into WPA2 Enterprise, RADIUS, 802.1X etc as this is just going to make it even more complex for people to understand and irrelevant for Home users as this used when connecting to Business/Enterprise networks.
Yesterday, my friend Victor wanted to crack a wifi network (his, of course) using his MacBook Pro.
I told him to use the excellent VirtualBox images of Kali Linux from Offensive Security and aircrack-ng.
I had just forgotten that:
- Using advanced wireless features is impossible from a virtual machine
- Even if he used Kali Linux with a dual boot, installing the wireless drivers to make it work with the airport card is tiresome.
- Most (not
airmon-ng) aircrack-ng tools can be installed on macOS with MacPorts, butairodump-ngandaireplay-ngcrash.
So PLEASE, if you want to do other advanced networking things than network sniffing or what is described in this article, do yourself a favour and buy an USB adapter to use with the virtual machine.
There is a list on the website of aircrack-ng, and I think the Alfa AWUS051NH v2 is great.Some people say it is expensive, but last time I checked on Google Shopping, it cost less than half an Apple mouse.
There are 3 steps:
- Identify the target acces point: name (= BSSID), MAC address (= SSID) and channel (~ radio frequency)
- Sniff the channel in monitor mode to retrieve:
- a beacon (easy)
- a handshake (= four-way handshake), or some frames of it (hard)
- Crack the password using the dump
What makes the retrieval of the handshake hard is that it appears only when somebody connects to the access point.
The good news is that you can deauthentificate people from the wifi network - it’s called wifi jamming and it’s useful to impress a girl and piss off people at Starbucks.When they reconnect, they re-send the handshake. That adds a Deauth step.
“Install”
Scan
It saves the .cap capture file and displays the path.
If you don’t have the beacon or the handshake, it will fail accordingly.
For wordlists, see below.
As I said, aireplay-ng doesn’t work on a MacBook Pro.The catch is that aireplay-ng can do a lot of other things besides deauth attacks.
You might read that airport cards do not support packet injection, but packet injections are for WEP attacks and nobody uses WEP anymore. We only want to send some deauthentification frames.
Use JamWiFi. A ready-to-use application is provided there.
What Is A Wpa Password For Mac
In fact, you can indentify the target with it too, and it has a really nice GUI.
Once you have selected the access point, you can deauth one or multiple users. Stop after about 50 “Deauths”, or else the persons might have trouble to reconnect during several minutes.
It might not work it you are too far from the target as your airport card is far less powerful than the router.
Using airport presents some issues. You cannot know if you got the beacon and the handshake until you stop the capture and try with aircrack-ng.
You capture a lot of unuseful packets too.
Using tcpdump is more efficient.
When you launch those lines, the first tcpdump easily captures a beacon and the second waits for the handshake.
Use JamWiFi to deauth some users, and when tcpdump shows you it got 4 frames or more, Ctrl-C. It appears you can use less that 4 frames, but it depends on the frames you got (for instance 1,2 or 2,3 are sufficient). Anyway you should normally get at least 4. If nothing shows, try to deauth another user.
Now you have everything in capture.cap. You can also run aircrack-ng on it.
Like aireplay-ng, aircrack-ng offers so many features that it cannot be the best in everything.
We can really speed up the process by using hashcat.
Install with brew
Convert with cap2hccapx
hashcat doesn’t take cap files, only hccapx files.
Just install hashcat-utils and use cap2hccapx
Alternatively, use this online tool.
Crack
This page provides some examples.
To use with a dictionnary:
You have a lot of other options, like brute force:
Refer to the documentation fot more patterns.
Speed

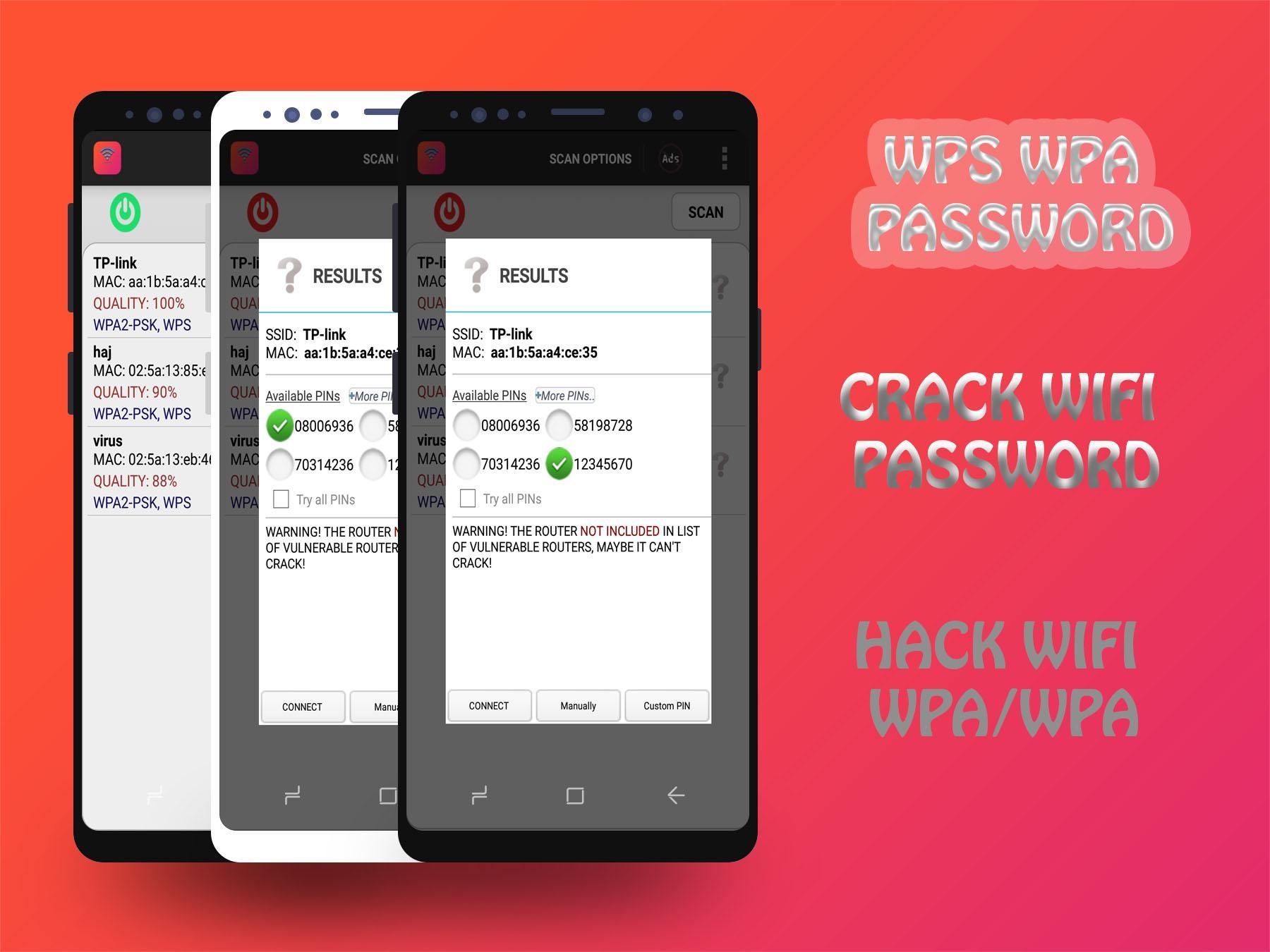
hashcat works on the GPU.
On my MacBook Pro, it yields a performance of 5kH/s: it tests 5000 passwords in a second.
On a Tesla K20m, the speed is 75kH/s. I managed to crack the 5 last lowercase letters of a wifi password in about 1 minute (26**5 // 75000 = 158 seconds to test them all).
We can see here that a GTX 1080 breaks 400kH/s.
Find My Wpa2 Password
I recommend:
For more efficiency, target the networks with silly names (good examples are “mozart”, “I love cats”, “Harry and Sally”), and avoid the ones called “National Security Agency”, “sysadmin” and “sup3r h4x0r”.
To find a password, you have to be lucky and have a good idea of its shape.
A lot of default wifi passwords are composed of 8 or 10 hexadecimal digits.
In average (worst case divided by 2) and according to the above benchmark, with a GTX 1080:
- 8 hexadecimal characters take 90 minutes.
- 10 hexadecimal characters take 16 days.
- 12 hexadecimal characters take 11 years.
What Is A Wpa Password For Mac Desktop
If you only want free wifi, just do MAC spoofing on a hotspot that uses web login.